Manage cases natively in Microsoft's unified security operations platform
Case management is the first installment of new capabilities for managing security work when you onboard to Microsoft's unified security operations (SecOps) platform.
This initial step toward delivering a unified, security-focused case management experience centralizes rich collaboration, customization, evidence collection, and reporting across SecOps workloads. SecOps teams maintain security context, work more efficiently, and respond faster to attacks when they manage case work without leaving the Defender portal.
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
What is case management (Preview)?
Case management enables you to manage SecOps cases natively in the Defender portal. Here's the initial set of scenarios and features supported.
- Define your own case workflow with custom status values
- Assign tasks to collaborators and configure due dates
- Handle escalations and complex cases by linking multiple incidents to a case
- Manage access to your cases using RBAC
As we build on this foundation of case management, we're prioritizing these additional robust capabilities as we evolve this solution:
- Automation
- Multi-tenant support
- More evidence to add
- Workflow customization
- More Defender portal integrations
Requirements
Case management is available in the Defender portal, and to use it, you must have a Microsoft Sentinel workspace connected. There's no access to cases from the Azure portal.
For more information, see Connect Microsoft Sentinel to the Defender portal.
Use Defender XDR unified RBAC or Microsoft Sentinel roles to grant access to case management features.
| Cases feature | Microsoft Defender XDR Unified RBAC | Microsoft Sentinel role |
|---|---|---|
| View only - case queue - case details - tasks - comments - case audits |
Security operations > Security data basics (read) | Microsoft Sentinel Reader |
| Create and Manage - cases and case tasks - assign - update status - link and unlink incidents |
Security operations > Alerts (manage) | Microsoft Sentinel Responder |
| Customize case status options | Authorization and setting > Core Security settings (manage) | Microsoft Sentinel Contributor |
For more information, see Microsoft Defender XDR Unified role-based access control (RBAC).
Case queue
To start using case management, select Cases in the Defender portal to access the case queue. Filter, sort, or search your cases to find what you need to focus on.
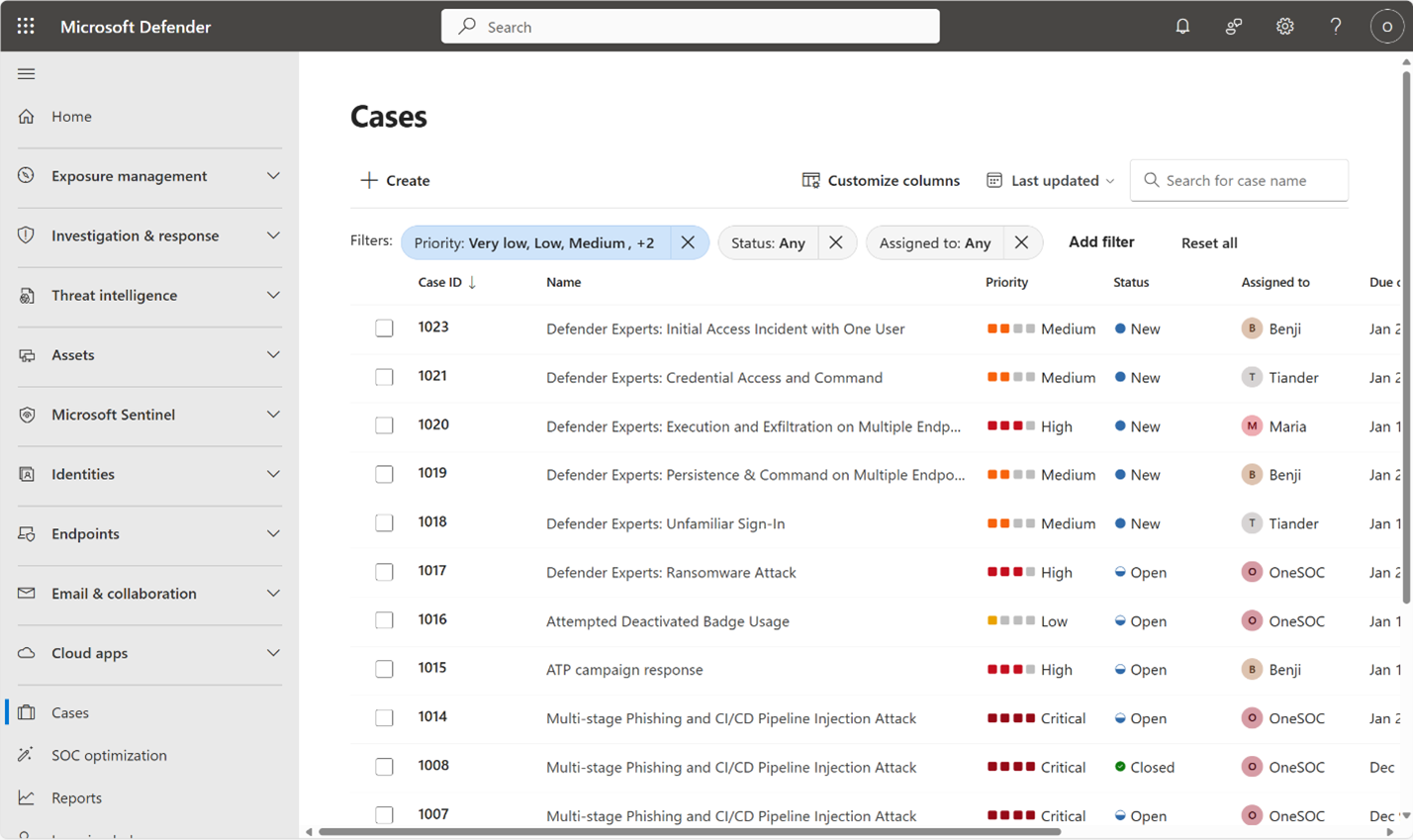
The maximum allowed per tenant is 100,000 cases.
Case details
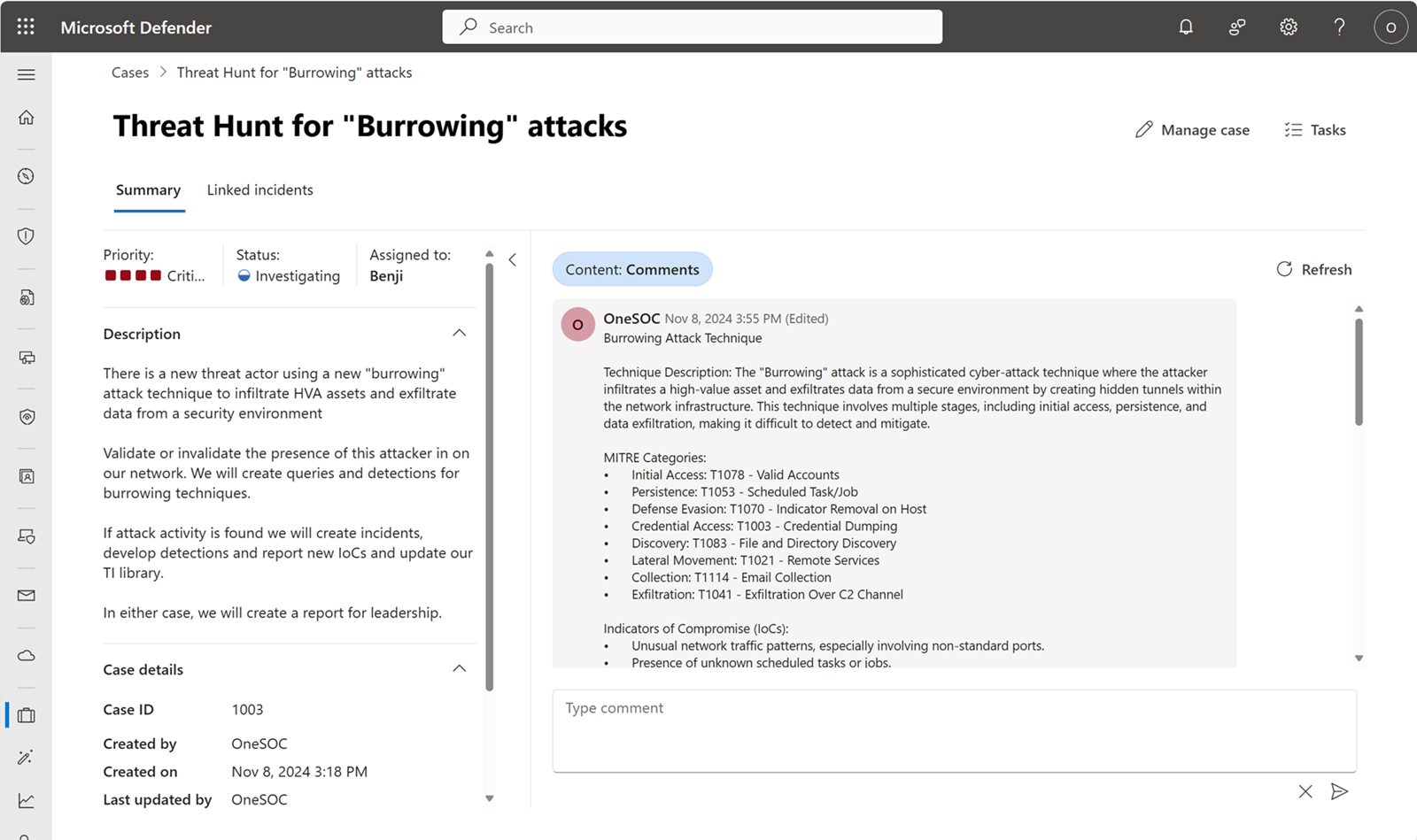
Each case has a page which allows analysts to manage the case and displays important details.
In the following example, a threat hunter is investigating a hypothetical "Burrowing" attack that consists of multiple MITRE ATT&CK techniques and IoCs.
Manage the following case details to describe, prioritize, assign, and track work:
| Displayed case feature | Manage case options | Default value |
|---|---|---|
| Priority | Very low, Low, Medium, High, Critical |
none |
| Status | Set by analysts, customizable by admins | Default statuses are New, Open, and ClosedDefault value is New |
| Assigned to | A single user in the tenant | none |
| Description | Plain text | none |
| Case details | Case ID | Case IDs start at 1000 and aren't purged. Use custom statuses and filters to archive cases. Case numbers are automatically set. |
| Created by Created on Last updated by Last updated on |
automatically set | |
| Due on Linked incidents |
none |
Manage cases further by setting customized status, assigning tasks, linking incidents, and adding comments.
Customize status
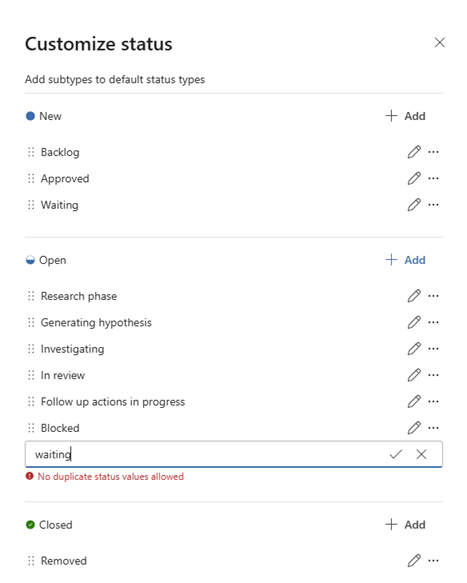
Architect case management to fit the needs of your security operations center (SOC). Customize the status options available to your SecOps teams to fit the processes you have in place.
Following the burrowing attack case creation example, the SOC admins configured statuses enabling threat hunters to keep a backlog of threats for triage on a weekly basis. Custom statuses such as Research phase and Generating hypothesis match this threat hunting team's established process.
Tasks
Add tasks to manage granular components of your cases. Each task comes with its own name, status, priority, owner, and due date. With this information, you always know who is accountable to complete which task and by what time. The task description summarizes the work to do and some space for describing the progress. Closing notes provide more context about the outcome of completed tasks.
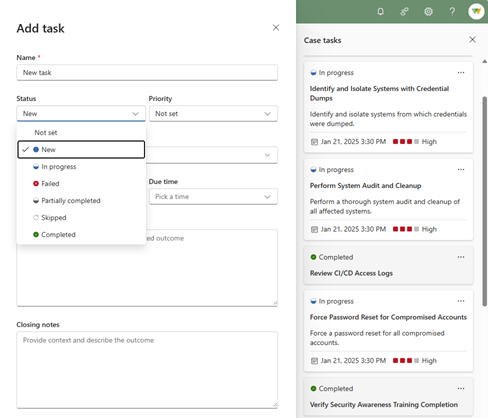
Image shows the following task statuses available: New, In progress, Failed, Partially completed, Skipped, Completed
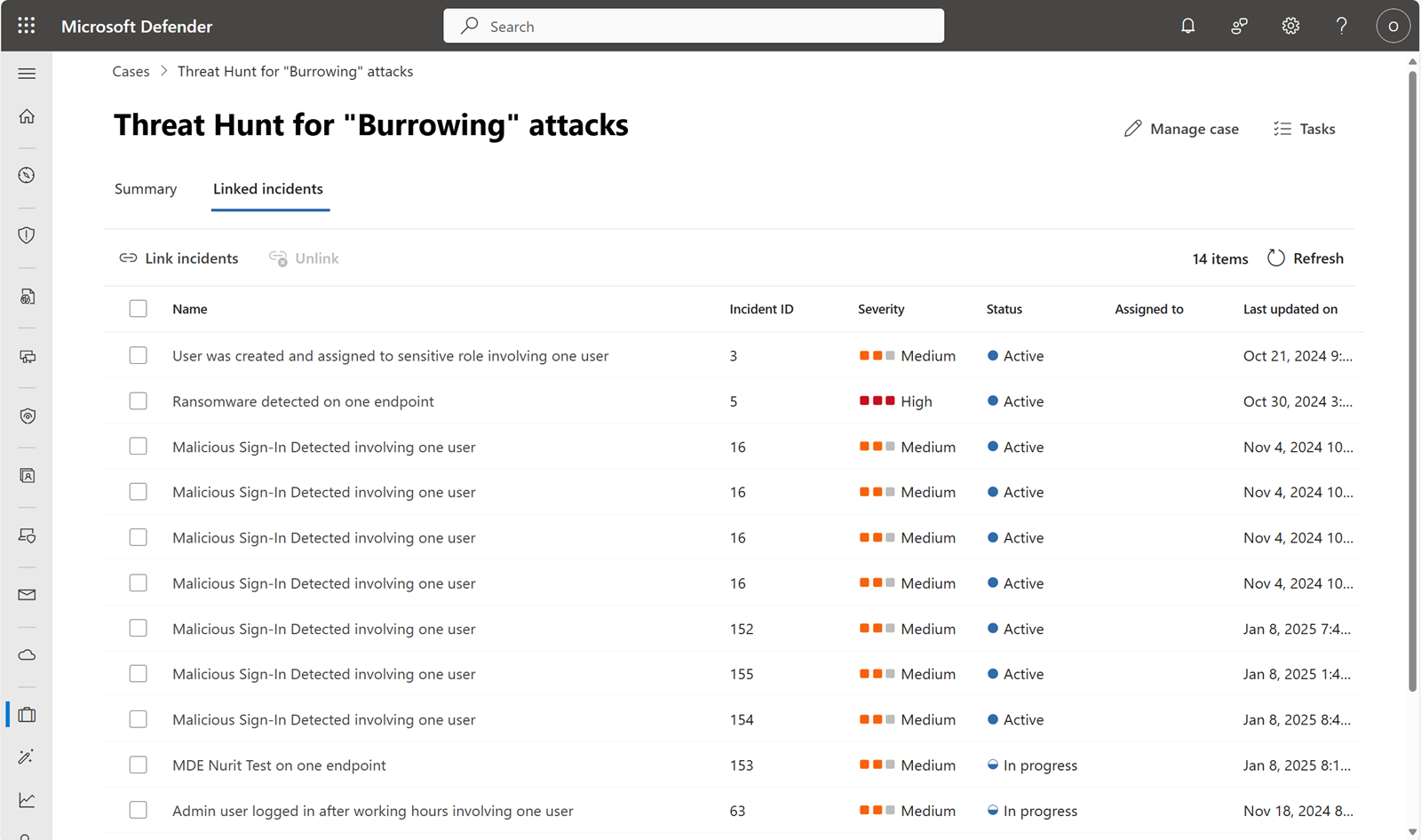
Link incidents
Linking a case and an incident helps your SecOps teams collaborate in the method that works best for them. For example, a threat hunter who finds malicious activity creates an incident for the incident response (IR) team. That threat hunter links the incident to a case so it's clear they're related. Now the IR team understands the context of the hunt that found the activity.
Alternatively, if the IR team needs to escalate one or more incidents to the hunting team, they can create a case and link the incidents from the Investigation & response incident details page.

Each case has a threshold of 100 linked incidents.
Activity log
Need to write down notes, or that key detection logic to pass along? Create plain text comments and review the audit events in the activity log. Comments are a great place to quickly add information to a case.
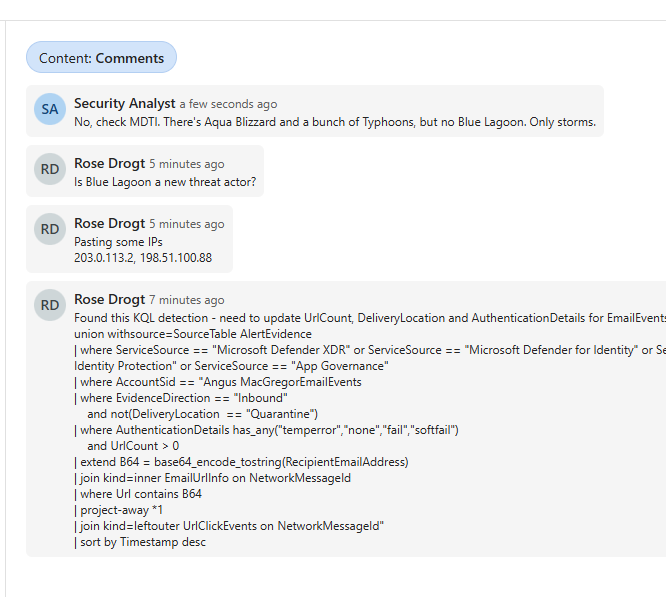
Audit events are automatically added to the activity log of the case and the latest events are shown at the top. Change the filter if you need to focus on comments or audit history.